- Client portal security is a trust issue, not an IT problem. One breach can cost you $149,000 and years of client relationships, making security your most powerful competitive advantage when done right.
- SaaS platforms outsource the security burden for less than the cost of one emergency consultant, while self-hosted WordPress plugins leave you responsible for every update, patch, and vulnerability that hackers actively exploit.
- Ask vendors the right questions before signing anything. Providers who confidently answer queries about encryption, 2FA enforcement, and third-party audits are worth paying for, while vague responses are red flags.
I hear this from agency owners all the time: “We know security matters, but honestly? We have no idea where to start.”
I get it. When you’re evaluating client portals, it’s tempting to focus on features like file sharing, project management, and white labeling. Security gets buried in the fine print, filled with terms like encryption at rest and SOC 2 compliance that feel deliberately confusing.
But here’s what I’ve learned building SPP.co and talking to hundreds of agencies: client portal security isn’t an IT problem. It’s a trust problem.
Every file your client uploads, every message they send, every invoice they pay through your portal is an act of trust. They trust you not just with their business, but with their data. If that trust is broken by a security breach, it doesn’t matter how good your work is. The relationship is damaged, maybe permanently.
This guide is for you, the agency owner or operations manager who doesn’t have a PhD in cybersecurity. We’re going to cut through the noise and talk about this like we’re grabbing coffee. My goal is to give you a practical, no-nonsense framework to protect your clients, your reputation, and your business.
Understanding this topic involves several interconnected concepts:
- Account Management
- Churn Rate
- Client Onboarding
- Client Portal
- CRM (Customer Relationship Management)
- Project Dashboard
Each of these concepts plays a crucial role in the overall topic.
Why security matters more than you think
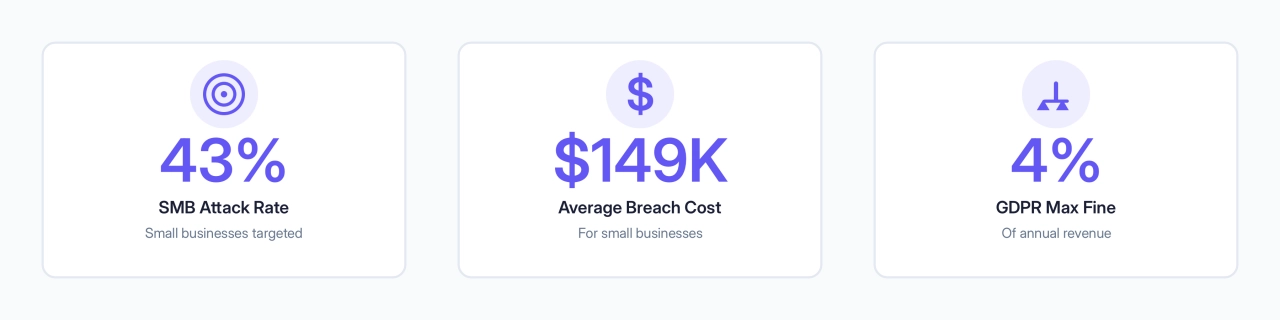
We tend to think of data breaches in terms of big corporations like Target and Equifax. But according to Verizon’s 2024 Data Breach Investigations Report, 43% of cyberattacks target small businesses. Why? Because SMBs often have weaker defenses but still hold valuable client data.
The consequences can be devastating:
Financial Loss: According to IBM’s 2024 Cost of a Data Breach Report, the average breach costs $4.88 million globally, with small businesses facing $149,000 on average. GDPR fines aren’t just for big corporations, small companies face penalties ranging from €10,000 to 4% of annual turnover. Add legal fees, notification costs, and potential client lawsuits, and a single incident can wipe out years of profit.
Reputational Damage: I’ve heard of agencies losing half their client roster after a breach, not because the work got worse, but because prospects Googled their name and saw data breach in the headlines. Trust takes years to build and seconds to destroy. It’s your most valuable asset, and it’s extremely difficult to rebuild once it’s gone.
Operational Chaos: Dealing with a breach is a full-time job. It pulls you and your team away from client work, derailing projects and grinding your business to a halt.
A cybersecurity consultant who talked to PurpleSec framed it this way:
Most SMBs are probably not focused on security. They’re more focused on profit and just developing their business. And now we as cybersecurity professionals need to translate the risk of cybersecurity and get small businesses to understand that there’s financial impact that could happen if they do have to, or if they realize a risk and suffer a data breach or a cyber attack.
 Bruno Aburto,
Booz Allen Hamilton
Bruno Aburto,
Booz Allen Hamilton
This disconnect is exactly the problem. Security feels abstract until it costs you a client, or worse, your business.
But let’s flip this around. Getting security right isn’t just about avoiding disaster. It’s a competitive advantage.
When you can confidently tell a prospect, “We take your data security seriously. Here’s how we protect you…,” you’re not just selling a service; you’re selling peace of mind. In a crowded market, being the trustworthy choice is a powerful differentiator. It becomes a core part of the client experience you deliver.
The core pillars of a secure client portal
So, what does a secure client portal actually look like? It’s not one single feature, but a combination of practices working together. Forget the jargon for a minute. It really boils down to four fundamental pillars.

Data encryption: protecting data in transit and at rest
Think of encryption as a digital lockbox. It scrambles your data so that even if someone gets their hands on it, they can’t read it without the key.
Encryption in Transit: This protects data as it moves between your client’s computer and your portal’s server. It’s what the “s” in
https://is all about. It prevents hackers from eavesdropping on the connection (like putting your conversation in a soundproof room). If your portal URL doesn’t start withhttps://, stop reading and fix that immediately. Seriously, right now.Encryption at Rest: This protects data while it’s just sitting on the server. This is surprisingly often overlooked. If a hacker manages to access the server’s hard drive, encryption at rest ensures all your client files and data are unreadable gibberish.
Access control: who can see what?
You wouldn’t give every employee the keys to your office, the file cabinets, and the company bank account. The same principle applies to your client portal. Strong access control ensures people can only see and do what they’re supposed to.
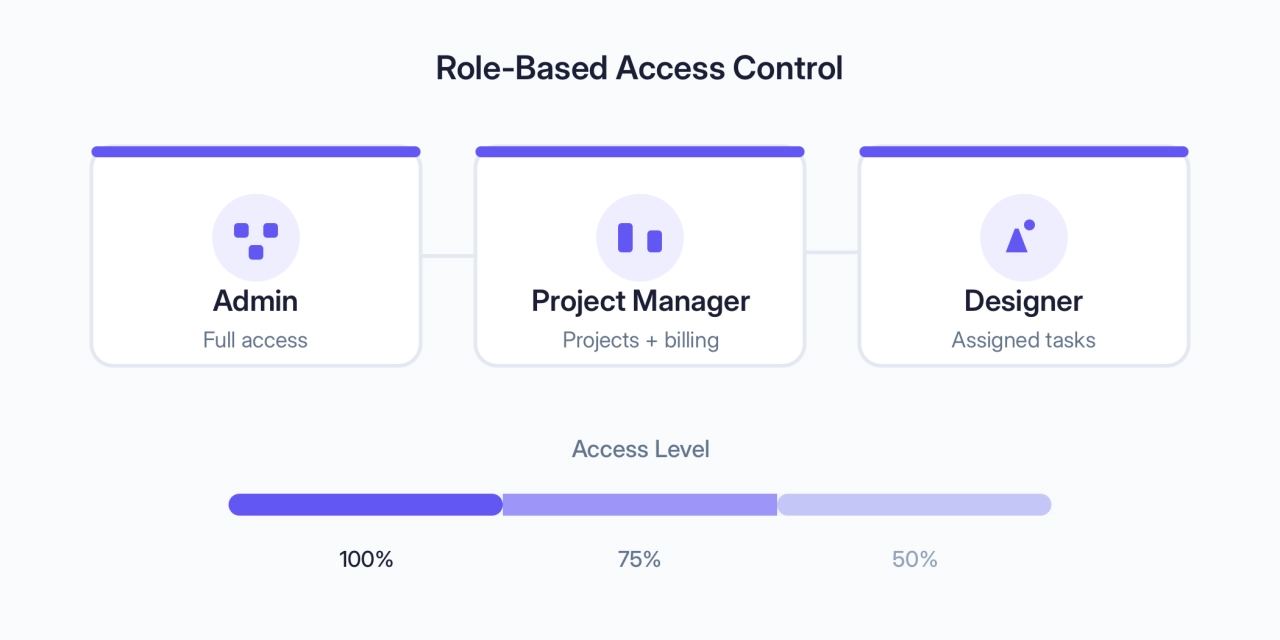
Role-based access control (RBAC): It means you can create different roles with different permissions. For example, a client should only see their own projects. A project manager might see all projects but not billing information. A junior designer might only see the specific tasks assigned to them. Without this, you risk one client accidentally seeing another’s confidential files. Having robust RBAC is one of the most must-have customer portal features.
Two-factor authentication (2FA): You use this every day with your bank or Google account. It’s that code they text you after you enter your password. Enforcing 2FA makes stolen passwords useless to an attacker. It’s one of the single biggest security upgrades you can make.
Single sign-on (SSO): For larger clients, SSO allows them to log in to your portal using their existing company credentials (like their Google or Microsoft account). It’s more convenient for them and more secure for you, as it centralizes user management and uses the security of major tech providers.
The reality? Some clients will push back. “It’s too complicated.” “Can’t I just use a strong password?” Here’s what I learned: frame it as protecting their business, not yours. “Your competitor would love to access your pricing strategy through the portal. This security step mitigates that risk.” Most come around. The ones who don’t? They’re usually the same clients who’d blame you after a breach.
Infrastructure security: the foundation of protection
This is the stuff that happens behind the scenes, but it’s the foundation everything is built on. It’s about the servers, networks, and data centers where your portal lives.
Secure hosting: Where is the portal hosted? Is it a cheap shared server or a secure, managed environment like Amazon Web Services (AWS) or Google Cloud? Top-tier providers have physical security, redundancy, and entire teams dedicated to protecting their infrastructure.
Firewalls & intrusion detection: Think of a firewall as a bouncer for your server, blocking malicious traffic before it can get in. Intrusion detection systems are the security cameras that monitor for suspicious activity and alert someone when something looks wrong.
Proactive monitoring: audits, logs, and vulnerability scanning
Security isn’t a set it and forget it task. A good platform is constantly on guard.
Audit logs: This is a running record of who did what, and when. Who logged in? Who downloaded a file? Who changed a password? If something goes wrong, these logs are essential for figuring out what happened.
Vulnerability scanning & penetration testing: This is like hiring a professional security firm to try and break into your portal. Reputable software providers do this regularly (it’s called pen testing) to find and fix weaknesses before criminals can exploit them. Ask potential vendors if they do this.
Key data privacy regulations explained
Now we’re going to tackle the legal stuff. GDPR, CCPA, HIPAA… it’s a mess of acronyms that can feel overwhelming. I’m not a lawyer, and this isn’t legal advice, but here’s the agency owner’s guide to what you actually need to know.
GDPR (General Data Protection Regulation)
Who it applies to: If you have or want clients in the European Union, this applies to you. It doesn’t matter where your business is located.
What it means in practice: GDPR is all about data privacy and user rights. For your client portal, this means things like:
The right to be forgotten: You must have a way to permanently delete a client’s data if they request it.
Data portability: A client can ask for a copy of all their data in a common format.
Consent: You need a clear reason for collecting any piece of data, and you need to document it.
In practice, this means your portal must allow complete data deletion within 30 days of a request. Choosing a GDPR compliant client portal is a fundamental requirement for doing business with EU customers.
CCPA/CPRA (California Consumer Privacy Act/California Privacy Rights Act)
Who it applies to: If you do business with residents of California (and meet certain revenue or data processing thresholds), this applies to you.
What it means in practice: It’s similar to GDPR, giving consumers rights over their personal information. Key things for your portal include being transparent about what data you collect and providing an easy way for users to opt out of their data being sold.
HIPAA (Health Insurance Portability and Accountability Act)
Who it applies to: If you handle any Protected Health Information (PHI) for clients in the healthcare space, HIPAA applies. This could be patient records, medical billing info, etc.
What it means in practice: Do not take this lightly. HIPAA compliance is very strict and requires specialized solutions. Generic client portals are almost never HIPAA compliant out of the box. If you work in healthcare, you need to use a portal provider that will sign a Business Associate Agreement (BAA) and has been specifically built for HIPAA. Seriously, don’t try to DIY this. It’s not worth the risk.
The critical decision: SaaS vs. self-hosted security
This is one of the most important decisions you’ll make, and it has major security implications. You essentially have two paths for your client portal: a SaaS (Software-as-a-Service) platform or a self-hosted solution (like a WordPress plugin).
The SaaS advantage: outsourcing the security burden
A client portal running on the SaaS model is one you pay a monthly or annual fee for, like SPP.co. The provider handles all the hosting, maintenance, updates, and (most importantly) the security.
This is the path I recommend for most agencies, and it’s why I built SPP.co. Why? Because you’re effectively hiring a dedicated security team for a fraction of the cost.
They worry, so you don’t have to: Enterprise-focused platforms like Huddle and agencies-focused solutions like SPP.co have engineers whose entire job is to monitor threats. They handle the firewalls, the encryption, the server maintenance.
Compliance is baked in: Reputable SaaS providers understand regulations like GDPR and build their platforms to help you comply. They have features for data deletion and export ready to go.
Predictable costs: You pay a flat fee. You're not going to get a surprise bill for an emergency security consultant when a new vulnerability is discovered. And when you measure the full ROI, security is just one piece of the return.
You’re not just buying software; you’re buying peace of mind and outsourcing a big responsibility.
SaaS vs. self-hosted: security responsibility breakdown
Security Area | SaaS (SPP.co) | Self-Hosted (WordPress Plugin) |
|---|---|---|
Infrastructure Security | Managed by provider (AWS) | Your responsibility to configure and maintain |
Security Updates | Automatic, immediate patches | Manual updates required for WP core, theme, all plugins |
Data Encryption | Built-in at rest and in transit | You must configure and verify |
Compliance Features | GDPR/CCPA tools included | You build from scratch or cobble together plugins |
Monitoring & Audits | 24/7 threat monitoring, regular pen testing | You hire security services or go without |
Disaster Recovery | Automated backups, redundancy | You set up and test backup systems |
True Monthly Cost | $129-1,500/month all-inclusive | $20 plugin + $50 hosting + $100 security + ongoing labor hours |
The self-hosted responsibility: when you are the security team
A self-hosted portal, most commonly a WordPress client portal plugin, can seem appealing. It often has a lower upfront cost and feels like you have more control.
But you have to be brutally honest about what that control means. It means you are 100% responsible for security.
The update treadmill: You are responsible for updating WordPress core, your theme, and every single plugin, immediately. A single outdated plugin can create a backdoor for hackers.
Configuration is on you: Did you configure the server firewall correctly? Is your database encrypted at rest? Do you have a system for malware scanning? You or someone on your team needs to be the expert.
The hidden costs: The plugin might be cheap, but what about the cost of premium hosting, a security service like Sucuri, and the hours your team spends on maintenance? The true cost of building a custom client portal is always higher than you think.
Going the self-hosted route is like choosing to build your own car instead of buying one from a manufacturer. It’s possible, but unless you’re an expert mechanic, it’s probably not going to be as safe or reliable.
Your actionable security checklist
Alright, let’s make this real. Here are the actionable steps you can take to make a smart decision and keep your business secure.
Questions to ask every potential vendor
Below is your vendor interrogation list. A good provider will answer these confidently, often with specifics.
Is data encrypted in transit AND at rest?
Can I enforce 2FA for all users?
What role-based access controls are available?
Where is the data physically hosted?
Do you conduct third-party security audits or pen testing?
What's your breach notification process?
How do you support GDPR/CCPA compliance (data deletion, export)?
What's your uptime SLA and disaster recovery plan?
If they dodge, give vague answers, or say “we’re working on that,” run.
Tip: You can find some of the best client portal software that already ticks these boxes by reviewing feature comparisons.
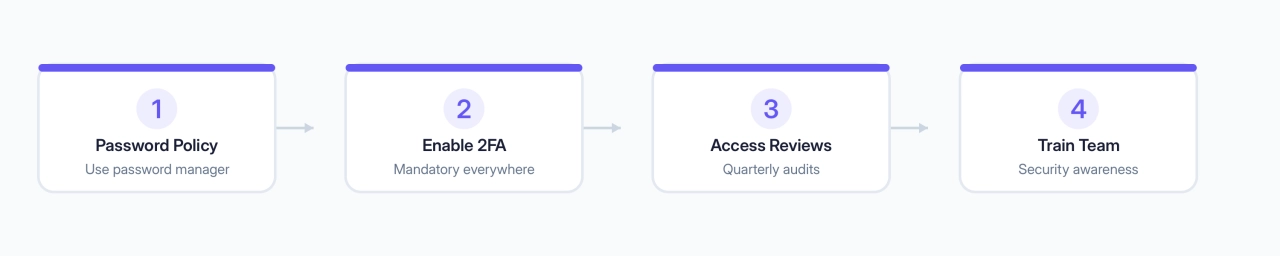
Internal policies to implement
Choosing a secure tool is only half the battle. The other half is how your team uses it. Here’s a simple process to implement.
How to communicate security to clients
Security conversations feel awkward because you’re asking clients to do more work—another password, another login, another security step. But the agencies that handle these conversations well don’t just avoid breaches, they win more deals. When you can confidently explain why you require 2FA or won’t email sensitive files, you’re demonstrating competence, not imposing restrictions.
Client Objection | Your Response | Why It Works |
|---|---|---|
“Can you just email me the files?” | ”Email isn’t encrypted—anyone intercepting it can read your files. The portal keeps everything organized, encrypted, and accessible only to you.” | You’re explaining the risk to them, not enforcing your rules |
”Do I really need another password?” | “Your account has pricing docs, strategy, and client data. 2FA means even if someone steals your password, they can’t access it. Takes 30 seconds.” | You made it about their data, not your security policy |
“Why can’t my intern have full access?” | “Let’s give them access to exactly what they need. When they leave, you won’t worry about them still having your financials or competitor analysis.” | You’re protecting their business, not restricting access |
“Should security be a line item in proposals?” | Enterprise: Yes—“Portal & Security Infrastructure: $X/month” with details. Everyone else: Bake it into your platform fee. | Enterprise expects itemization; others just want to know it’s handled |
“When do I mention security during sales?” | Work it in naturally: “Files live in our secure portal—no email hunting.” For regulated industries, lead with: “We’re SOC 2 compliant and GDPR-ready.” | Security becomes a feature, not a checkbox |
The key is framing security as something you do for clients, not to them. You’re protecting their pricing strategy, their client lists, their competitive advantage. Most clients stop pushing back once they understand the stakes—and the ones who don’t are usually the same ones who’d sue you after a breach.
Should you get cyber liability insurance?
Short answer: probably yes.
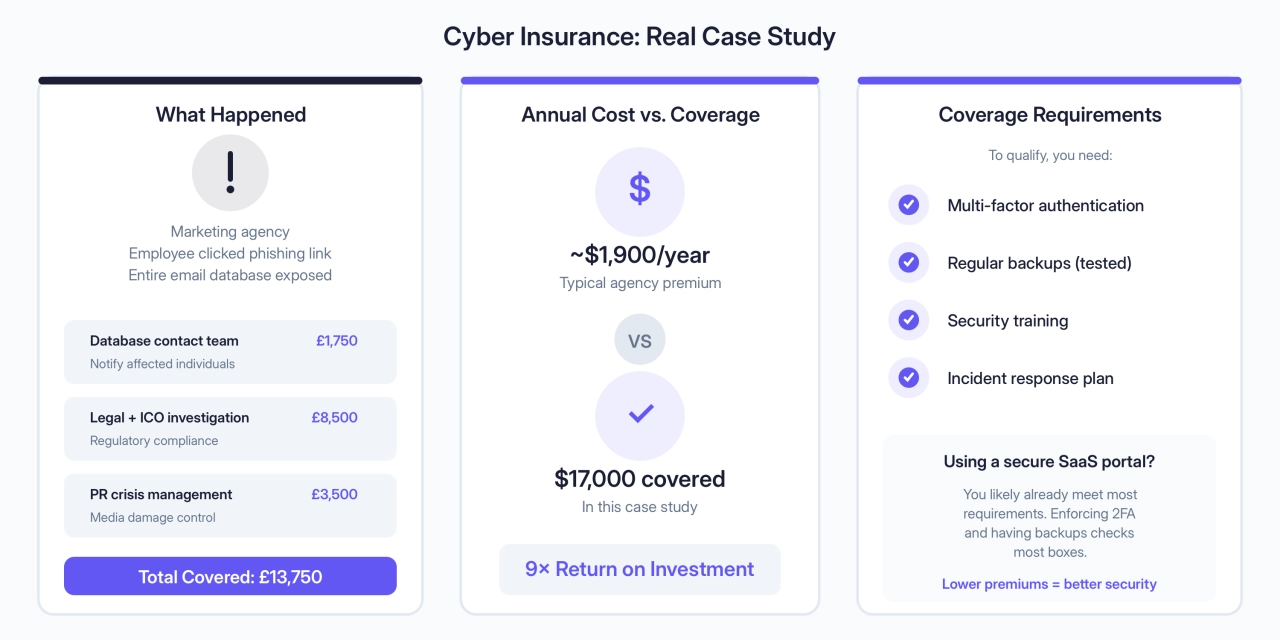
Here’s a real example from a PolicyBee case study: A marketing agency was launching a luxury hotel campaign. Account manager was exhausted, got a security alert email asking him to reset his password. He clicked. It was a phishing scam. Cybercriminals now had access to their entire email database.
What cyber insurance covered:
£1,750 for a team to contact everyone on the list and handle the flood of complaints
£8,500 for legal experts to notify the ICO, handle the regulatory investigation and eventual fine
£3,500 for PR crisis management when the press got hold of the story
Total cost covered: £13,750 (about $17,000)
The agency survived. Without insurance? They’d have paid that out of pocket, plus potentially faced lawsuits from everyone on that list. Most small agencies would’ve shut down.
What it costs: According to Insureon’s 2024 data, small businesses pay a median of $1,740/year for cyber insurance. Marketing agencies typically fall in the $1,800-$2,000 range. Cost depends on how much client data you handle and your security measures (MFA, backups, training all lower your premium).
What insurers require: Most policies need minimum security standards before they’ll cover you:
Multi-factor authentication (do you require it?)
Regular backups (are they tested?)
Employee security training (documented?)
Incident response plan (do you have one?)
If you’re using a secure SaaS portal with 2FA enforced, you’re checking most boxes.
The catch: Insurance doesn’t cover willful negligence. If you ignored obvious risks or violated your own policies, they might deny your claim. That account manager who clicked the phishing email? Covered, because anyone can make that mistake. But if the agency had disabled all security measures? Different story.
When to get it: Before you handle sensitive client data. Before you sign your first enterprise contract (they’ll ask for proof of coverage). Before something happens that costs you $150,000 you don’t have.
Talk to an insurance broker who specializes in tech/agency coverage. Expect detailed questions about your security practices. If you can’t answer confidently, fix your security first, then get insured.
What to do if you get breached
Hope for the best, plan for the worst. If you discover a breach, the first 48 hours determine whether you survive it or shut down. Here’s what to do, in order.
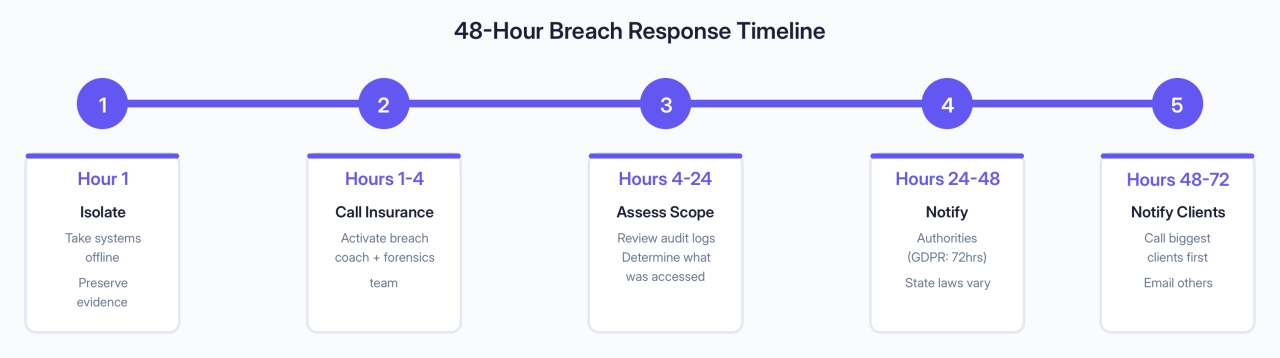
Your actual emergency contacts:
Cyber insurance provider: [Policy number, 24/7 phone]
Your lawyer: [Contact, specialization in data breach]
Forensics firm: [Your insurance provides this, but know the process]
Team lead for breach response: [Who’s in charge internally?]
That marketing agency survived because they acted fast and notified everyone properly.
The agencies that don’t make the news? They’re the ones who tried to handle it quietly. Maybe they waited a week to tell clients, hoping to fix it first. Or they notified some clients but not others. Or they didn’t report to regulators because it wasn’t that bad. Then someone found out—a client noticed suspicious activity, a journalist got tipped off, or the regulator came knocking during a routine audit.
Now they’re facing the original breach costs plus regulatory fines for late notification (GDPR fines can hit 4% of annual revenue), plus lawsuits from clients who feel deceived, plus the reputation damage from news coverage that focuses on the cover-up, not the breach. Most don’t recover. The ones that survive spend years rebuilding trust they destroyed in 48 hours of bad decisions.
Frequently asked questions
How do I make a client portal secure?
Start with three non-negotiables: encryption in transit (HTTPS) and at rest, enforced two-factor authentication for all users, and role-based access control so people only see what they need. Choose a SaaS provider that handles infrastructure security, or if self-hosting, budget for dedicated IT security expertise.
What are the legal requirements for a client portal?
It depends on your clients’ location. GDPR applies if you serve EU clients (requires data deletion within 30 days and export capabilities). CCPA applies for California clients above certain thresholds. HIPAA applies if you handle any healthcare data and requires specialized, compliant solutions with a signed Business Associate Agreement.
What security features should a client portal have?
HTTPS encryption, encryption at rest, 2FA, role-based access control, history logs, automatic backups, and SOC 2 Type II certification. Also verify the provider does regular penetration testing, offers 99.9%+ uptime SLA, and makes data export easy if you leave.
Is a self-hosted client portal secure?
Only if you have dedicated IT expertise. You're 100% responsible for WordPress updates, plugin patches, server firewall configuration, database encryption, malware scanning, and threat monitoring. A single outdated plugin creates vulnerabilities hackers actively exploit. Most agencies are safer with managed SaaS platforms.
What questions should I ask a client portal provider about security?
Ask: Is data encrypted in transit and at rest? Can I enforce 2FA? What are your role-based access capabilities? Where is data hosted? Do you do third-party security audits? What's your breach response process? How do you help with GDPR/CCPA compliance? What's your uptime SLA?
What happens if my client portal gets breached?
First 4 hours: Isolate systems, call cyber insurance (delays void coverage), don’t delete evidence. Within 24 hours: Determine what data was accessed. Within 72 hours: Notify regulators if required (GDPR mandate). Within 3 days: Notify affected clients directly. Offer credit monitoring if personal info exposed.
Conclusion: security is an ongoing commitment
I get it, this was a lot. If you started reading this feeling like security is overwhelming, you’re not alone.
The key takeaway is this: you don’t have to be a security expert, but you do have to be a responsible business owner. And being responsible means making informed decisions.
It means understanding that choosing a cheap, insecure solution can cost you everything. It means recognizing that the ongoing cost of a secure SaaS platform isn’t an expense; it’s an investment in trust, reputation, and business continuity. It means knowing what questions to ask and what internal habits to build.
By thinking through these things now, you’re not just buying a tool or checking a box. You’re building a more resilient, professional, and trustworthy business. And in the long run, that’s the foundation that allows you to stop worrying about disasters and focus on what you do best: delivering amazing work for your clients.
Disclaimer: This guide provides practical security insights based on industry experience, not legal or professional security advice. Consult qualified professionals for your specific situation.